HTB Busqueda
01 Sep 2023SPOILERS AHEAD
Busqueda is an Easy rated box on HackTheBox and was the first box I ever finished with minimal guidance. It makes use of outdated software versions with an exploit openly available on the web as is pretty common with other Easy rated boxes. Password reuse allows for a good amount of lateral movement and misconfigured sudo permissions is at the heart of allowing for extensive information gathering on this box.
Enumeration
We will first run an nmap scan. Notice that port 80 is open indicating an HTTP web server is open.

First add searcher.htb to the /etc/hosts file.

Then browse to the default webpage. We may also type in the IP address into the search engine since /etc/hosts will perform name resolution.

Scrolling to the bottom of the page reveals a technology being used: Searchor 2.4.0. A Google search for this version reveals a proof-of-concept (POC) exploit for remote code execution.

User Foothold
First set up a nc listener on the attacker machine listening on port 9001. Then run the GitHub POC exploit with arguments being the hostname of the web server and the attacker machine IP address.

The nc listener will respond back with a reverse shell in which we can find the contents of the user flag.


Probing around the filesystem, we can find exposed credentials for the cody user within a file in the .git directory.

Password reuse is found by attempting to use this password to invoke sudo for the current svc user. We find that we can execute one specific python script as the root user.

Running the -h options reveals what command we can run with system-checkup.py.

Here is sample output from each of the commands:
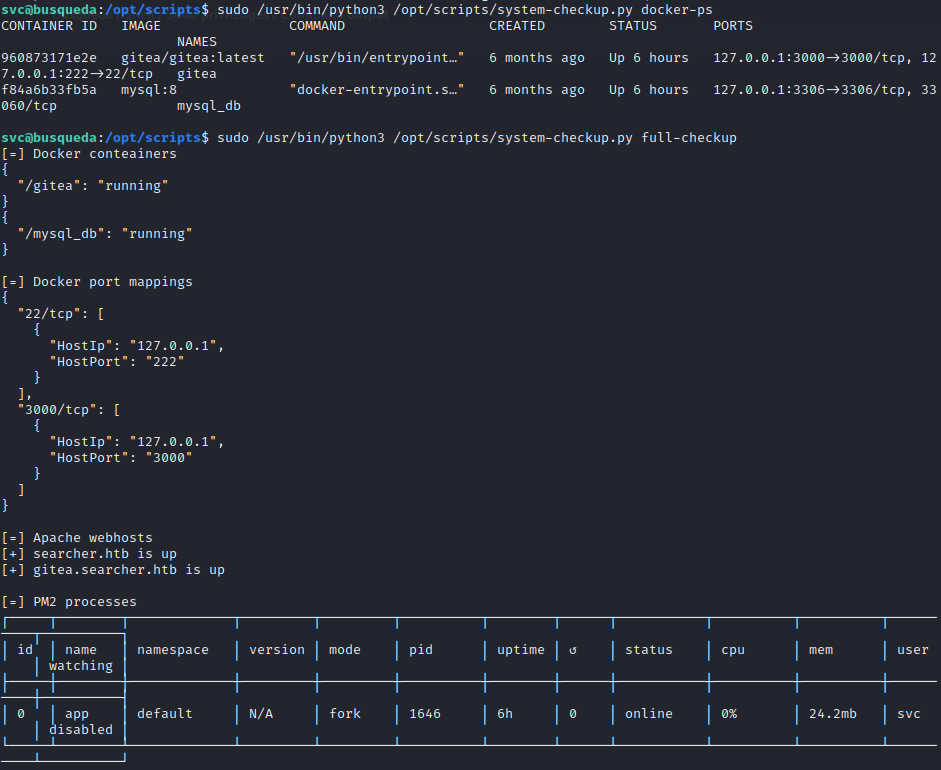

Looking closer, the output of the full-checkup command reveals a virtual host: gitea.searcher.htb.
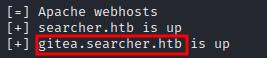
Add this as an entry to the /etc/hosts file and navigate to the default webpage. On here there is a login page. Don’t forget to try default credentials. However, in this case it doesn’t work.

Another one of the commands, docker-inspect, actually ends up revealing a MySQL database password.
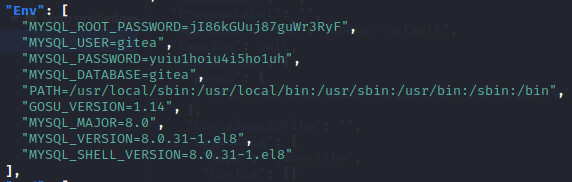
Trying the combination of administrator:yuiu1hoiu4i5ho1uh happens to give access to the gitea administration interface.

Privilege Escalation
In this interface, we can inspect the source code of system-checkup.py. Unfortunately we can’t modify the code, even as the administrator, which would result in a simple Python reverse shell payload being appended to the end of the source code and being called whenever we ran system-checkup.py back in the shell.
We find something else that is interesting however. The full-checkup command is being called using a relative path. Because of this, we can create our own full-checkup.sh script and have the system-checkup.py script run our own script as the root user. That doesn’t sound good…

Create the full-checkup.sh script in a directory that the svc user owns with the following bash reverse shell:

Set up a nc listener and run the full-checkup command using sudo.

And congratulations, you are now the root user with access to the root flag.
